OnlyKey is like a YubiKey, but more versatile.
The most widely known security key is probably the YubiKey. I've had a YubiKey 5c and YubiKey Nano for several (4+) years now, and have had an OnlyKey for around a year. YubiKeys are useful and convenient for OTP codes, and also FIDO/U2F, but having only 1 button is a big limiting factor.
The OnlyKey feels a lot more versatile. Here are some thoughts on what's good and bad about the YubiKey and the OnlyKey, and why I much prefer and recommend an OnlyKey instead for most.

I intended this post to be a short post with just enough info to remind myself how and why I use the OnlyKey, but I got a little carried away (more on that later...), and it ended up long enough to justify setting up markdown-it-table-of-contents which also lead to markdown-it-anchor. Enjoy!
Contents
- YubiKeys are okay
- OnlyKey regular features and usage
- Its glorious buttons
- 6 buttons: 2 profiles & self-destruct
- 2 actions per button, per profile. Passwords, OTP, key combinations etc.
- Only set password entry on long button presses, and probably avoid automating submit.
- Key layout: OTP short press, password long press, profile e-mail at the end.
- SSH setup is super easy, using Trezor's agent
- Other useful OnlyKey features
- Is OnlyKey a good idea?
- What do others think of the OnlyKey?
- Conclusion
YubiKeys are okay
They're smaller and with fewer features than the OnlyKey, but probably hold the "nobody ever got fired for buying IBM" status amongst security keys.
YubiKey for OTP works reasonably well, even on Android in places
Adding YubiKey as OTP device works really well in most cases. E.g. adding YubiKey as a second factor on an AWS account just requires to you press the button in the console saying you want it, and then press the button on the YubiKey when prompted, and you're done.
I also added YubiKey as a second factor to my preferred password manager, KeepassXC, as that supports mobile devices. With the 5c, I was able to plug it into my phone's usb, and unlock KeepassXC on Android. I even designed and 3D printed a small watch strap mount for my 5C for easier access! (OpenSCAD or blender-rounded 3MF file, if you're interested.)
YubiKey and GPG enables a lot but is lots of moving parts.
I ended up leaning a lot on GPG to get the functionality I wanted from the YubiKey, but that lead to a lot of moving parts. You need to have GPG all setup, generate keys on your device, setup smartcard mode, configure your SSH agent, ensure the appropriate daemons are running etc.
Even with some very comprehensive documentation, some things just felt janky:
- Ensuring the GPG agent was up and running correctly was challenging, and I'd often have to run some extra steps when I used my YubiKey to get it working.
- Using GPG for SSH, on different flavours and configs of linux, particularly with multiple terminal open across multiple apps, it was 50/50 as to if the PIN prompt would come through on the active TTY.
- The number of slots on the YubiKey was finite in a lot of cases, so at the time, only 1 GPG identity was conveniently supported.
- Using GPG effectively allowed me to avoid having to directly use
ykman, the yubikey manager.
Ultimately, the YubiKey felt like just an OTP/authenticator type device. I wanted a convenient and versatile security key.
OnlyKey regular features and usage
Its glorious buttons
Immediately, you can understand why this device is more versatile. The keypad. It offers an obvious solution to the TTY pin problem I had with the YubiKey:

The buttons are similar to the YubiKey's capacitive touch, this means no moving parts. The rubber case that comes with the OnlyKey has button holes that guide your finger tips to the right place. If anything, the buttons are almost too easy to press, but do need to be pressed by something conductive, like a human.
6 buttons: 2 profiles & self-destruct
Once setup, to use the OnlyKey, you plug the device in and enter a pin code. There are 3 possible configurable pins:
- 2 pins for 2 different profiles
- 1 self destruct
Putting in a profile pin unlocks the key and turns on a different colour light to indicate the profile. That profile is a completely separate and unique set of keys, passwords and configuration.
This is super helpful: 1 profile for work, 1 profile for personal, determined by the pin you initially enter to unlock the device.
Enter an incorrect pin 10 times, or enter the self destruct pin, and the OnlyKey wipes itself. Without the self-destruct, a 6 digit keypad would be feasible to brute force any convenient length value.
2 actions per button, per profile. Passwords, OTP, key combinations etc.

When the OnlyKey is unlocked, pressing any of the individual buttons briefly will trigger an action, which can be customised in the desktop app. Holding a button for 1.5s will trigger a different action.
These actions can be different authenticator OTP codes, or keying in different passwords, or even key combinations for common shortcuts.
Only set password entry on long button presses, and probably avoid automating submit.
Key entry configuration can do complex stuff. I was able to setup a spare Google account login to happen, including entering the username, pressing return, entering a password, waiting a few short seconds, then entering a 6 digit authenticator OTP code, and pressing return.
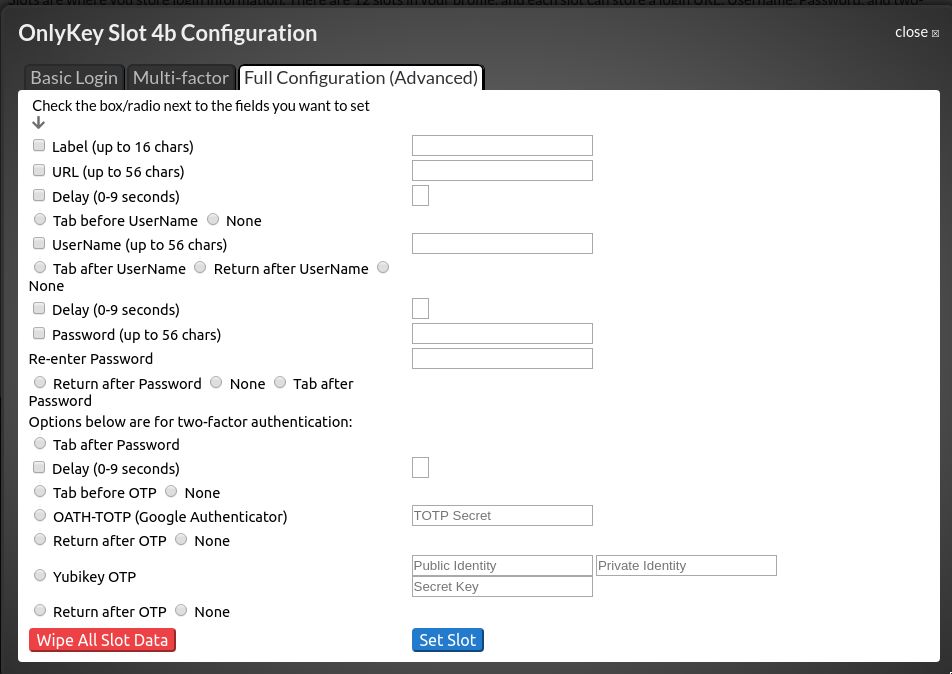
Although it was satisfying to know I could do this, it was a bad idea. Accidentally pressing the button anywhere else apart from the username field on a Google login page was... chaotic. It would definitely, eventually, lead to accidentally typing out a username and password and sending it in a Slack channel or Teams chat or similar.
Key layout: OTP short press, password long press, profile e-mail at the end.
- 1 - short press: password manager OTP
- 1 - long press: password manager extra long complex password
- 2 - short press: IDP 1 OTP
- 2 - long press: IDP 1 extra long complex password
- 3 - short press: some other service OTP
- 3 - long press: some other service extra long complex password
- 6 - short press: profile e-mail
I use a variation of this setup. Each number corresponds to a service, with the e-mail often being the username for these services. Pressing 6 will type my e-mail anywhere. Having OTP on short press also means most accidental presses - at worst - dump a random number, rather than a secret.
SSH setup is super easy, using Trezor's agent
This is probably one of my favourite features of the OnlyKey. It uses libagent, the same approach as the Trezor security key SSH agent and also supports the Ledger Nano S hardware wallet.
To onboard a new service, generate the authorized_keys entry with onlykey-agent:
$ onlykey-agent username@host
ssh-ed25519 ASAAC3NzaC1lPOTATOIDwqxTbTLthb0MSgGeSXZEUEOHZwxJ/M7EJfXPt7Z8iM <ssh://username@host|ed25519>The username@host part is used as a seed to derive a unique pair from a single private key on the device. This is a really satisfying solution to being able to the problem of only being able to store a finite set of unique identities.
Then to use that with something that uses SSH:
$ onlykey-agent username@host -- git pullSome handy aliases
2 terminal aliases help here too, 1 for the git command itself, and one for other commands that might depend on git creds, such as installing packages from private repos:
alias okgit="onlykey-agent myusername@github.com -- git"
alias okg="onlykey-agent myusername@github.com --"
okgit pull
okg yarn install A quick poke around the implementation - accessible, but a bit rough
SSH with OnlyKey really is almost too convenient. I assumed this did some pure bash funky subshell stuff, overriding some magical SSH_* env vars I wasn't aware of to set a default identity. Poking through the source for onlykey-agent though, I was wrong. It's basically all Python, and implements its own SSH client, with each supported hardware device defining its own interface to its cryptographic functions for that SSH client to use.
When you invoke onlykey-agent, it grabs all your parameters. Based on those, it then gathers everything else required. It then create the SSH client connection using the implementation above. When using it with single commands, any parameters after -- are passed to the SSH client to run. If creating an interactive shell with -s, it grabs SHELL env var and uses that as the command to run your standard terminal experience.
It's not the most beautiful or cared for Python code in the world, but it gets the job done. Someone who seems far smarter and did a far more thorough anlysis of this agrees.
Other useful OnlyKey features
OnlyKey challenge codes - necessary evil.
Some OnlyKey functions have a challenge code. This means you will be prompted to enter some digits on the OnlyKey itself when you use onlykey-agent. You can turn this off, but I leave it on. The purpose is to ensure functions can't be done without physically having access to the key. If this is disabled, anyone one who has compromised the computer over the internet could use the key, meaning the unique physical factor to the authentication is lost.
The challenge code is implemented largely in the OnlyKey specifics part of libargent and I haven't really experienced the same TTY issues I had with GPG agent pin entry setup for the YubiKey. The YubiKey issue was exacerbated by also needing to provide input to the TTY, but with OnlyKey, the input is done via the buttons on the key itself.
It can be a little inconvenient having to enter a bunch of codes for each private dependency on larger projects still, but it can be disabled in the onlykey-app.
Backing up a security key isn't always possible or a great idea
Creating backups for security keys can be an awkward topic. A truly secure hardware key will have some unique special configuration that exists only on that device's hardware and cannot be extracted. Even if your computer is riddled with malware, OTP and signatures from a secure USB security key should still be relatively safe as the malware can't get to the secrets in the hardware device. But if you can backup that unique special configuration, then someone can get to that backup remotely, they could load that backup onto a blank key and all of a sudden you're compromised.
Even if they can't get to the backup, if they can remotely access your machine with the key connected, and initiate a backup of the key from the computer, you're going to have an equally bad time.
But OnlyKey does it in quite a cool way
With OnlyKey, unlock the key with a profile pin, and then hold down the 1 key for 5+ seconds, and it will type out its own backup of that profile:
-----BEGIN ONLYKEY BACKUP-----
CbE3xf0RXmX5eajdD1LSqlZ1c1gn2JqMO8Psqy2/eT15T+kmhR1pmqHW/7jnW//Um1+K0j4Y/4jZ
...7 lines removed for brevity & paranoia...
s1z9dz+z2swrJs4tyk+i8SkV3mkOAV5HEEijrUkfRCR247vGIYLvcqWde5um/49NregP+pQ7w1H0
PfQIveqIyqPnI/szmjqVx97XmfESCJTlf4JLRDNl
--FXsW/gSy55Gneb+Soau0PoF1Eu5Q6M/shRxCiZJeIiw=
-----END ONLYKEY BACKUP-----
Restoring can be done by setting an OnlyKey with the same backup pin, and then using the onlykey-app. Backups are per profile.
If you want a super-safe setup, you shouldn't be really be able to even take a backup of a security key, but then if you lose the key, you're equally up the creek. Yubico's answer to backups is also vague on specifics.
For my own personal use though, I assess the risk and convenience of this type of backup mechanism and approach to be significantly more appealing than the risk and convenience of not being able to backup a key, and having to have 2 actively setup keys in existence.
Hold 2 for a reminder of button functions
When configuring the OnlyKey, you can label each slot. Unlocking the key and then holding down the 2 key will type out all the slots and labels as a reminder of how the profile is configured. This works even without the app. E.g. the output for the key layout suggestions above would be:
1a passmanager OTP
2a idp OTP
3a someother OTP
4a
5a
6a email
1b passmanager pass
2b idp pass
3b someother pass
4b
5b
6b
For OnlyKey on-the-go visit https://apps.crp.to
One thing I did notice when putting this together though, is that you have to hold the 2 key for 5 seconds to get this output. On a couple of occasions, I didn't hold for long enough and dumped idp pass password.
I haven't really used this functionality, but I still think it's cool it exists and can be used without any setup using keyboard input.
Is OnlyKey a good idea?
On the whole, I think so, yes - but it's not perfect.
Not a full replacement for a password manager
There are not enough slots for lots of passwords, but a desktop password manager also is more convenient in most cases. Most of my computer usage is at my home desk, with my OnlyKey within arms reach plugged into my dock. Accessing the OnlyKey is convenient but still requires me to relinquish control of a mouse or keyboard. Password managers can have an awareness of what's being logged into, so can find and instantly populate all of those fields automagically. OnlyKey requires you to press a button to tell it what it should do.
So for convenience and scale, I aim to have my most commonly used or not-password-manager-managed passwords configured on some of the OnlyKey long press actions, and the remaining ~75% in KeepassXC.
Less popular and less oversight than YubiKey
Very few people I speak to are aware of the OnlyKey. Lots of who have worked in tech have heard of YubiKey. Yubico who do the YubiKey are also a relatively large company with a large enterprise customer base. This should bring tighter controls, more stringent processes, more sets of eyes etc. It can also leads to diffusion of responsibility and other scale related quality and security issues.
The OnlyKey, is by CryptoTrust:
CryptoTrust is an innovative provider of specialized secure solutions for businesses and individuals. As an independent security-consulting firm, CryptoTrust’s consultants have years of industry experience in Cybersecurity and internationally recognized security credentials. The specialized experience of CryptoTrust in the DoD and financial services industries enables development of customized security products and services that meet high assurance security standards.
The OnlyKey app, website, docs and generally everything else associated with them makes them out to feel like a significantly smaller operation. This isn't necessarily bad, but it means the OnlyKey probably isn't as battle-tested as YubiKey.
Rough, but opensource and actively developed code
My own personal assessment is that some of the OnlyKey python code is not the best. But I also think it feels like it's written by security nerds, rather than software engineering nerds. I don't think there's anything wrong with this and would probably be my preference. However, it does mean software engineering nerds will and do have meltdowns about how it looks.
The OnlyKey is fully open source. You can even get the device firmware. Even if the code is a little bit messy, at least that's possible to see, acknowledge and fix, which wouldn't be the case with closed source alternatives. The developer(s?) of OnlyKey actively respond to reviews and posts of their code too.
YubiKey firmware is largely closed source. They have a blog post on it which is basically a very long way of them saying "it was too much money, time and/or effort with too much risk". I see why they took that decision, that's their tradeoff for their target market. Whether the OnlyKey is a good idea probably comes down to the intended use and market.
Is it secure? Relatively, for the right people, like me, I think
Indeed, some people will scoff at the OnlyKey:
the marginally lower levels of entropy in the hardware random number generator might introduce predictability into key generation leading to blah blah blah
or
that chip is potentially susceptible to hardware decapsulation and probing for physical malicious fault injection blah blah blah
But security often comes down to behavioral economics. Could someone hack this OnlyKey? Like most things: probably somehow. However, nothing I have access to is worth the incredible amounts of time and focus that would be required to successfully coordinate and execute these attacks.
Nothing is 100% secure. If you are the sort of person who is likely to be targeted by people capable of successfully identifying, intercepting and tampering specifically with your security hardware, then maybe these high effort attacks become a concern. Rather than state sponsored attackers though, for most individuals, the biggest threats are probably script-kiddie automated attacks, keylogging malware and password leaks/reuse. Based on this, I think the OnlyKey would be an appropriate and legitimate improvement for the security of most.
What do others think of the OnlyKey?
I found a few interesting other discussions on the internet. Internet security nerds are capable of incredible analyses and brutal conclusions. Here are a couple of notable things I found
The OnlyKey implementation is definitely messy and controversial
If you're of a technical persuasion, then I think these 2 links are the best resources for an independent assessment of the OnlyKey implementation:
- Hackernews post with a bunch of nerds tearing into it
- dev.to/mpixel with a less critical but thorough analyses of the SSH key derivation, including the challenges of following it - very well done.
They demonstrate extensively that the code is controversial. It's probably not written by a large mature development team, but more likely by 1 or 2 individuals. The code is hard to follow at times, including for people far far more capable than me, and there are a fair few little quality issues.
The creators aren't perfect, but clearly know some stuff
The discussion in those 2 links gets quite hard and overly critical in places I think, particular the HN post. However, the authors continue to respond, pointing out a lot of misconceptions in places, and actively accepting and pushing fixes for legitimate issues raised.
I don't think software without issues is possible, so all we can really aspire for is software with active, enthusiastic and capable maintainers.
As much as I like the user experience, others don't
These 2 reviews are less technical and more about usage and experience:
- https://www.scrye.com/wordpress/nirik/2020/04/03/onlykey-review/
- https://jekko.com/2018/11/19/onlykey-color-review-best-u2f-security/
They both don't recommend the OnlyKey, but for less technical reasons such as an ugly engineer's UI, or security concerns for entering the physical pin in a coffeeshop, or criticisms about the durability of the keychain or branding. These don't really impact me but support the argument that these things aren't for everyone.
Conclusion
What is "secure enough" is relative, and depends on your threat model which will be informed by your own risk appetite based on your circumstances. For the vast majority of people, if you're looking for another factor for an MFA setup, OnlyKey is definitely more secure than nothing, and more versatile than most.
OnlyKey is a newer and less popular security key than others, and as a result, it's still a little bit rough around the edges. This might make it inappropriate for those who might be target of APTs or state sponsored attackers, but if you're one of those people, you probably know that. However, the creators do know their stuff, and are actively improving OnlyKey.
And finally, the OnlyKey is a fun little device to nerd around with, far more so than a YubiKey. 🤓